A total of 69,189 Pakistani bank cards worth an estimated $3.5m have shown up for sale on the dark web.
Group-IB, an international company that specialises in preventing cyberattacks, says it is the second big sale of Pakistani bank cards in the past six months – and an “advanced, financially-motivated threat actor” may be behind the theft.
A pair of new databases were released on Joker’s Stash, one of the most popular underground hubs of stolen card data, at the end of January.
The vast majority of the unauthorised digital copies of the cards and PIN codes were related to a single bank, Meezan Bank Ltd.
Dmitry Shestakov, the head of Group-IB’s сybercrime research unit, said: “The scale, volume, frequency, and connection to one institution contributes to the theory that the leak might be involved in a larger incident, potentially an advanced actor gaining access to card systems within Pakistan.”
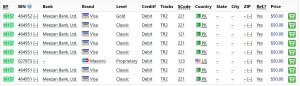
How does it work?
Crooks who buy the cards on dark web forums can use card dump data to produce cloned credit cards.
Money mules then use these fake cards to either withdraw money from ATMs or buy goods in, which are later resold by fraudsters.
Another scheme involves using the cards to buy non-existent goods from dummy companies. And many scammers buy crypto using stolen card details.
In November 2018, the Group-IB threat intelligence team reported on the leak of 177,878 payment cards linked to Pakistani and other international banks.
The banks affected by this breach included major Pakistani financial organisations such as Habib Bank, MCB Bank Limited, and Allied Bank Limited.
Disclaimer: The views and opinions expressed by the author should not be considered as financial advice. We do not give advice on financial products.
