Zcash was launched on top of Zerocoin protocol back in 2016. The protocol was described by Johns Hopkins University professor Matthew D. Green and his graduate students, Ian Miers and Christina Garman in 2013.
Zcash later switched to an upgrade of Zerocoin called Zerocash which brought even more anonymity, making the network more efficient as well. It now supports fast block times (75 seconds), low fees (default 0.0001 ZEC) and large block sizes (2 MB).
Many other projects including PIVX, Veil and NavCoin emerged around the same time but all of them gave up on Zerocoin by 2019, following the discovery of a computer bug which allowed hackers to steal coins during transactions.
Privacy concern
Remember that blockchains are meant to be anonymous. The way you appear on the Bitcoin network, for example, is through an address which is a random sequence of numbers and letters. None of your personal details are retractable from this address.
Transactions, however, are visible to everyone, which makes the system transparent. In case somebody manages to link your identity to a certain address (when you make a public donation, for example), all of your previous and future transactions on the blockchain are suddenly deanonymised.
Some Bitcoin holders use mixers to obfuscate the tracing process. With mixers, random accounts agree to create a shared pot of Bitcoin which is then split, creating a dozen of new accounts and transactions. There are certain trust issues associated with such services, and 100% success is still not guaranteed.
As a step further, Monero commits to some form of mixing by pooling transactions together and signing them with a ring signature.
Zcash and its use of Zero Knowledge Proofs (ZKP) help conceal everything including the sender, recipient and the amount. The only things reflected on the blockchain are the time of transaction happening and fees paid.
What is a zero-knowledge proof ?
Imagine that there is a circular cave separated by a door. Alice knows a magic spell which opens the door and she wants to convince Bob that she knows it without actually revealing it.
Alice enters the cave while Bob waits outside. She approaches the door either from the left or from the right with a 50/50 chance. Bob has no idea of where Alice went.
After that, he goes inside and shouts out a direction from which he wants Alice to appear. If she has to pass through the door, her knowledge of the spell will be confirmed when she returns to Bob as he requested.
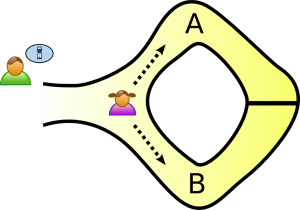
But what if she got lucky and went back by the same path? Well, if this experiment is run many times, her chance of being lucky every time decreases dramatically. With just seven rounds, the probability goes below 1%.
Notable flaws
In practice, ZKPs use mathematics and require large prime numbers in particular. Initially, these numbers were generated by a trusted third party for many coins including Zcash and Zcoin (now Firo). Anybody in possession of these numbers can create new coins for free. This is like not having any doors in the cave in the first place.
This kind of backdoor was found within Zcash cryptography protocol back in 2019, which allowed potential hackers to mint an arbitrary amount of shielded tokens.
Developers discovered the vulnerability in 2018 but spoke out about it only a year later when it was fixed. The issue was subtle and would have required a cryptography expert to understand it. The company claimed that nobody exploited the weakness, although it is not clear how they were able to see it given the highest level of anonymity.
Edward Snowden has notably applauded the team for eliminating the flaw.
As we discuss below, some users may choose to make their accounts transparent, which will reduce the anonymity level for anyone interacting with such wallets.
Zcash wallets
There is a way for Zcash users to make their transaction details visible. Transparent addresses are used in this case, while shielded addresses provide full anonymity. It is even possible to send funds from a shielded address to a public one and vice versa, in which case the transaction amount becomes known. See an example here.
The owner of a shielded wallet is able to disclose his transactions at any point using view keys. This feature can become useful when a regulator decides to audit your activity.
How to get Zcash
Zcash is running on an independent blockchain but its base code was borrowed from Bitcoin. It therefore uses Proof of Work for consensus and can be mined like any other PoW coin.
There is a 21 million cap on the total supply of tokens, with almost 12.5 million coins already mined by the time of writing this post.
ZEC is tradable on most crypto exchanges, although some countries have restricted access to it.
Conclusion
Zcash builds on top of modern cryptography to provide the highest level of security and privacy on the blockchain. Since human factor is involved in creating protocols, some problems can arise, although the team aims to respond to all issues responsibly.
Disclaimer: The views and opinions expressed by the author should not be considered as financial advice. We do not give advice on financial products.
